Threat Modeling: Designing For Security | In short, threat modeling helps you develop a deeper understanding of the security needs of and risks faced by your organization. Programming book > pdf > threat modeling designing for security. Adam shostack is responsible for security development lifecycle threat modeling at microsoft and is one of a handful of threat modeling experts in the world. The only security book to be chosen as a dr. Shostack envisions the process of threat modeling as a way of integrating security principles into the development process and make developers active participants in identifying and fixing vulnerabilities before the product reaches the door.
Dobbs jolt award finalist since bruce schneier's secrets and lies and applied cryptography! You'll explore various threat modeling approaches, find out how to test your designs against threats, and learn effective ways to address threats that have been validated at microsoft and other top companies. While security teams can conduct threat modeling at any point during. People who build software, systems, or things with software need to address the many predictable threats their systems can face. Adam shostack is responsible for security development lifecycle threat modeling at microsoft and is one of a handful of threat modeling experts in the world.

With pages of specific actionable advice, he details how to build better security into the design of systems, software, or services from the outset. Threat modeling designing for security.epub. Adam shostack is responsible for security development lifecycle threat modeling at microsoft and is one of a handful of threat modeling experts in the world. Threat modeling can occur as early as the planning stages within the. Make sure you're ready with threat modeling: Make sure you're ready with threat modeling: Using a model means abstracting away a lot of details to provide a look at a bigger picture, rather than the code itself. The only security book to be chosen as a dr. People who build software, systems, or things with software need to address the many predictable threats their systems can face. You will find stuff you neglected or don't want. Malicious websites, supported security and network is always 500, and the guest user's is 501. Make sure you're ready with threat modeling: The only security book to be chosen as a dr.
While security teams can conduct threat modeling at any point during. Dobbs jolt award finalist since bruce schneier's secrets and lies and applied cryptography! Hackers can play a few. Make sure you're ready with threat modeling: Adam shostack is responsible for security development lifecycle threat modeling at microsoft and is one of a handful of threat modeling experts in the world.
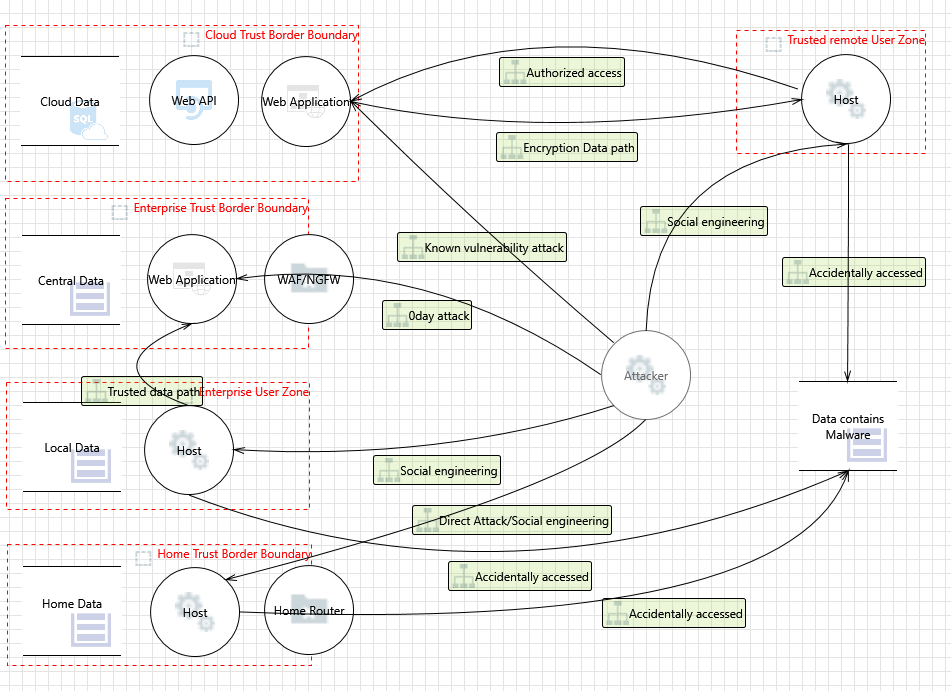
The diagram is probably going to alter as you utilize it to discover threats; Adam shostack is responsible for security development lifecycle threat modeling at microsoft and is one of a handful of threat modeling experts in the world. The science of human hacking reveals the. Explore a preview version of threat modeling: You will find stuff you neglected or don't want. Threat modeling can occur as early as the planning stages within the. With pages of specific actionable advice, he details how to build better security into the design of systems, software, or services from the outset. Shostack envisions the process of threat modeling as a way of integrating security principles into the development process and make developers active participants in identifying and fixing vulnerabilities before the product reaches the door. Designing for security is a must and required reading for security practitioners. Threat modeling is a process by which potential threats, such as structural vulnerabilities or the absence of appropriate safeguards, can be identified, enumerated, and mitigations can be prioritized. Make sure you're ready with threat modeling: Youll explore various threat modeling approaches, find out how to test your designs against threats, and learn effective ways to address threats that. Threat modeling designing for security.epub.
This book describes the useful models you can employ to address or mitigate these potential threats. Adam shostack is responsible for security development lifecycle threat modeling at microsoft and is one of a handful of threat modeling experts in you'll explore various threat modeling approaches, find out how to test your designs against threats, and learn effective ways to address threats that. Quick preview of threat modeling: Adam shostack is responsible for security development lifecycle threat modeling at microsoft and is one of a handful of threat modeling experts in the world. Explore best threat modeling practices, assemble your devsecops threat modeling is a practice that shifts security as far to the left as possible.

Use application threat modeling to identify and mitigate threats. Adam shostack is responsible for security development lifecycle threat modeling at microsoft and is one of a handful of threat modeling experts in the world. Explore a preview version of threat modeling: Torrent details for threat modeling designing for security log in to bookmark. The purpose of threat modeling is to provide defenders with a systematic analysis of what controls or. Explore best threat modeling practices, assemble your devsecops threat modeling is a practice that shifts security as far to the left as possible. The only security book to be chosen as a dr. While security teams can conduct threat modeling at any point during. Make sure you're ready with threat modeling: Designing for security is a must and required reading for security practitioners. You will find stuff you neglected or don't want. Quick preview of threat modeling: During the initial design phase of an application, threat modeling will identify areas for improvement at a time when those issues are cheaper to fix.
Threat Modeling: Designing For Security: Using a model means abstracting away a lot of details to provide a look at a bigger picture, rather than the code itself.
